Android is a mobile operating system that functions similarly to Windows (.exe) and Linux (.deb) in terms of software installation. Instead of .exe or .deb files, Android uses .apk (Android Package) files to install applications on mobile devices.
What is Android VAPT?
Android Vulnerability Assessment and Penetration Testing (VAPT) involves analyzing Android applications for security flaws. It consists of two main approaches:
- Static Analysis – Examining the application’s code and structure without executing it.
- Dynamic Analysis – Analyzing the application’s behavior while it is running.
Static Analysis
Tools Required
- apktool – Used to decompile and extract APK files.
- dex2jar – Converts Dalvik bytecode to a human-readable Java format.
- VS Code – A code editor for analyzing decompiled source code.
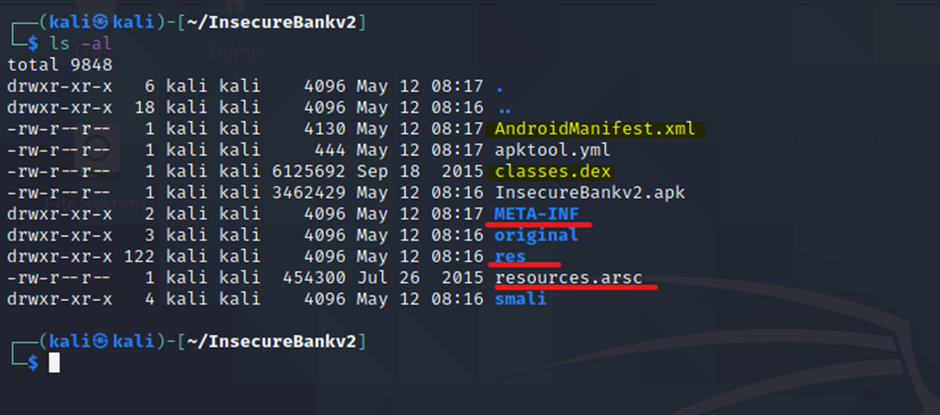
APK Structure Breakdown
When an APK file is extracted, it contains the following core components:
1. AndroidManifest.xml
This file defines essential application settings, including permissions and components like:
- Activities: Manage user interactions within the application.
- Services: Background processes that run continuously.
- Broadcast Receivers: Handle system-wide events.
- Content Providers: Manage shared data access between applications.
- Intents: Facilitate communication between different components.
- Implicit Intent: Opens media files using third-party applications.
- Explicit Intent: Opens files within the same application.
2. Classes.dex
This file contains the compiled code for the application in Dalvik bytecode format. Using dex2jar, we can convert it into a human-readable Java format for further analysis.
3. resources.arsc
This file stores binary resources, including strings, colors, and UI-related data that the application uses.
4. res/
This folder contains user interface components such as layouts, images, and language resources.
5. META-INF/
This directory holds cryptographic signatures, package metadata, and other security-related information for the APK.
Practical Analysis Using apktool
To extract an APK file, we use the following command:
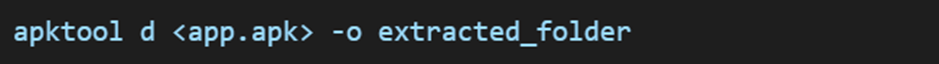
After extraction, the resulting folder contains all the key files and directories mentioned above. This allows security researchers to inspect and analyze the application for vulnerabilities such as hardcoded credentials, insecure API calls, or excessive permissions.
By performing a thorough static analysis, we can identify critical security issues before moving on to dynamic analysis and real-time behavioral testing.
Dynamic Analysis
In this part of the android VAPT, Dynamic Analysis part of the android application is mentioned.
Tools Required
- Genymotion
- Frida
- VirtualBox
Dynamic Analysis
For Dynamic Analysis, performing VAPT on any application running at the production level and can be used publicly. Some important techniques
- Installing Frida
- Root Detection Bypass
- Installing Genymotion
Installing Frida
- Install ADB driver
- Now you need to download Frida-server of 32bit or x86 for android architecture. For that, you need to run the following command.
- Now you need to install the Frida tool, using python2
because there are some dependencies of python2 so first we will install pip2 for python2.
Note: Just follow the instruction in the mentioned gist link.
Root Detection Bypass
What is Root Detection Bypass?
Well, When you have something in your brain and you suddenly decided to root your android device and try to run the application in your rooted device then it tends to allow users to run code with root permissions. This means that users can have full control over what their phone is doing. Rooting is the process of enabling root access to an Android device.
So, most android applications have checks to detect the rooted device at the time of installation or running the application and we need to bypass the check-in order to successfully perform root detection bypass.
- First, connect the android device with adb driver
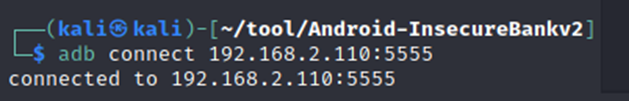
Adb connect to android device
2. Now push the frida server using add to android device tmp folder
3. After pushing the frida-server, now we need to run the server in order to intercept the running services in the android device
4. when you start the server, you need to intercept and display the services running inside the android device.
It will display a list
A detailed list of services running
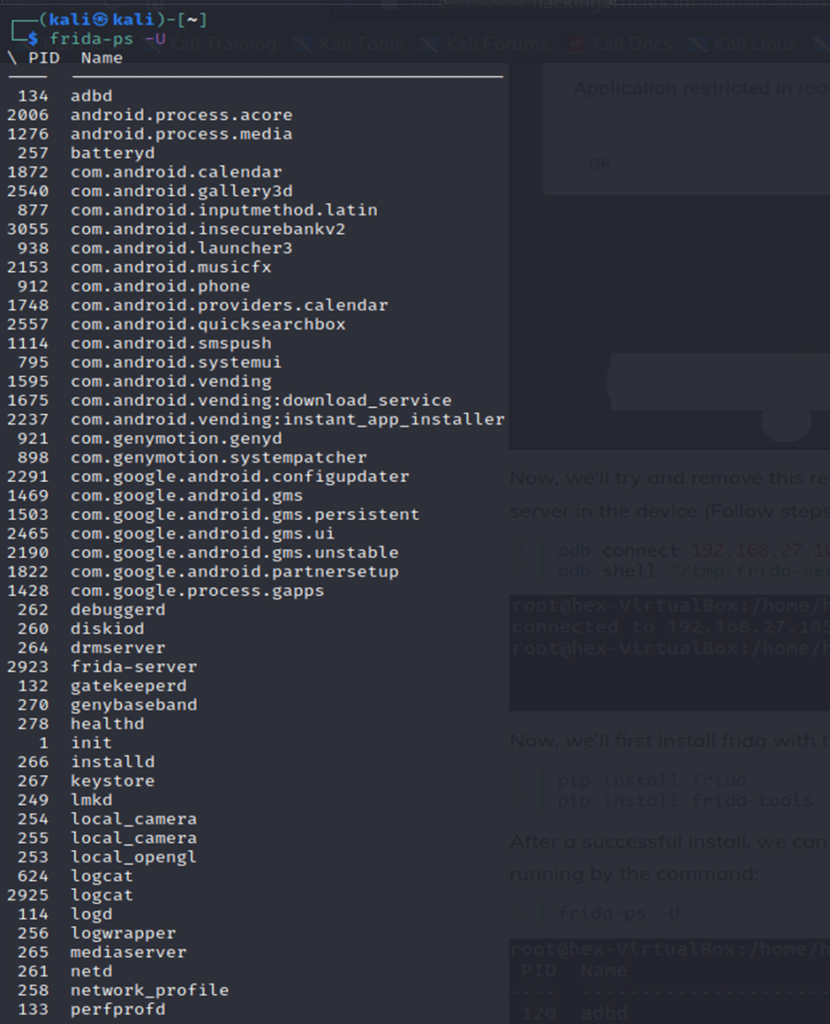
5. Now for root detection bypass you need to take help from here.
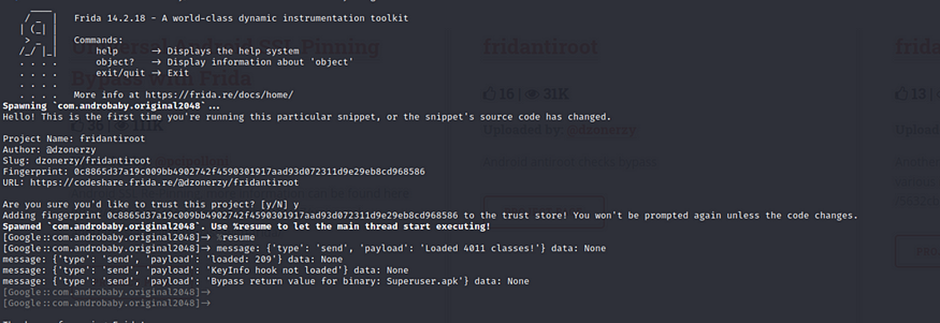
6. type %resume and wait to restart the application. If the root detection alert is gone after restart then you successfully bypass the root detection.
Process to Use Genymotion for Android Testing
Step 1- Installing Genymotion
- Run the Installer
- Double-click the downloaded .exe file.
- Follow the on-screen instructions to install Genymotion.
- If you chose the version without VirtualBox, install VirtualBox separately.
- Launch Genymotion
- Open Genymotion and sign in with your Genymotion account (register if you don’t have one).
- Create a Virtual Device
- Click + Add
- Choose an Android device (e.g., Pixel 4, Samsung S10).
- Select an Android version and download it.
- Start the Virtual Device
- Click Start to launch the Android emulator.
1.Give execution permission
2. Run the Installer

3. Move to /opt/ for System-wide Installation
4. Run the Installer

5. Sign in & Add a Virtual Device
Step 2- Configure and start genymotion
2.1 Launch Genymotion and Sign In
- Open Genymotion and log in with your account.
2.2 Add a Virtual Device
- Click “+ Add” to create a new virtual Android device.
- Select an Android version and device model.
- Download and install the selected device.
2.3 Start the Virtual Device
- Select the created device and click “Start” to launch the emulator.
Step 3: Connect Genymotion with ADB
3.1 Install ADB (Android Debug Bridge) If Not Installed
- Install ADB on your system:
sudo apt install adb # For Linux
choco install adb # For Windows (Using Chocolatey)
brew install adb # For macOS
3.2 Connect the Emulator to ADB
adb devices
Step 4: Install and Test Applications
4.1 Install an APK for Testing
- Transfer an APK to the emulator using:
adb install <app.apk>
4.2 Interact and Debug the App
- Open the installed app and test its functionality.
- Use adb logcat to monitor logs in real-time:
adb logcat
Step 5: Perform Security Testing
5.1 Network Traffic Interception with Burp Suite
- Set up Burp Suite to capture network traffic.
- Configure Genymotion’s Wi-Fi proxy settings to use Burp’s proxy address and port.
- Install Burp’s CA certificate on the emulator to decrypt HTTPS traffic.
5.2 Dynamic Analysis with Frida
- Install Frida for runtime manipulation:
adb push frida-server /data/local/tmp/
adb shell chmod +x /data/local/tmp/frida-server
adb shell /data/local/tmp/frida-server &
5.3 Static Analysis with apktool
apktool d <app.apk> -o output_folder
Step 6: Analyze Findings and Report
- Identify vulnerabilities like Insecure Data Storage, Improper Authentication, and Hardcoded Credentials.
- Document the test results and suggest remediation steps.
OWASP Mobile Top 10 for Android Penetration Testing
1. Improper Credential Management
Improper handling of credentials, such as hardcoding usernames and passwords, can allow attackers to extract sensitive information.
Key Risks
- Hardcoded credentials in source code
- Credentials stored in plaintext within local storage
- Transmission of credentials over insecure channels
- Weak password policies
Mitigation Strategies
- Avoid hardcoding credentials in the app
- Use secure keychain mechanisms for storing sensitive data
- Encrypt credentials before storing or transmitting
- Implement strong authentication mechanisms (e.g., MFA)
2. Inadequate Supply Chain Security
Attackers can inject malicious code into third-party libraries or modify the app during the build process, leading to security breaches.
Key Risks
- Malicious code injection in third-party libraries
- Exploitation of unpatched vulnerabilities in external SDKs
- Unauthorized modifications in the app’s build process
Mitigation Strategies
- Use only trusted and vetted third-party dependencies
- Regularly update and patch external libraries
- Implement integrity checks to detect unauthorized modifications
- Validate the security of third-party SDKs before integrating
3. Insecure Authentication and Authorization
Weak authentication mechanisms allow unauthorized users to gain access to restricted resources.
Key Risks
- Insecure Direct Object References (IDOR)
- Weak or broken session management
- Storing authentication tokens in insecure locations
- Exposing authentication endpoints to attackers
Mitigation Strategies
- Use strong authentication mechanisms (OAuth, JWT, MFA)
- Implement secure session management (short expiration, token rotation)
- Encrypt authentication tokens in storage and during transmission
- Restrict access based on user roles and permissions
4. Insufficient Input and Output Validation
Failure to properly validate user input and output can lead to SQL Injection, XSS, and Command Injection attacks.
Key Risks
- No input sanitization leading to injection attacks
- Inadequate encoding of user-generated content
- Failure to validate data exchanged over networks
Mitigation Strategies
- Use strict input validation techniques (allowlist instead of blocklist)
- Implement output encoding to prevent XSS
- Use parameterized queries to prevent SQL injection
- Verify all data exchanged between client and server
5. Insecure Communication
Apps that transmit sensitive data over plaintext or weak encryption can be intercepted by attackers.
Key Risks
- Sending data over HTTP instead of HTTPS
- Weak encryption algorithms (e.g., deprecated TLS versions)
- Exposure of sensitive data in URLs or request headers
Mitigation Strategies
- Enforce HTTPS (TLS 1.2+ recommended)
- Use strong encryption for all transmitted data
- Avoid exposing sensitive data in GET requests (URLs)
- Implement SSL pinning to prevent MITM attacks
6. Inadequate Privacy Controls
Privacy vulnerabilities expose Personally Identifiable Information (PII), leading to potential legal and reputational risks.
Key Risks
- Apps requesting excessive permissions without justification
- Data collection without proper consent
- Storing sensitive user information in plaintext
Mitigation Strategies
- Request only the necessary app permissions
- Encrypt sensitive user data both in storage and transit
- Implement user consent mechanisms before collecting data
- Securely delete user data when no longer needed
7. Insufficient Binary Protections
If an app lacks proper security measures, attackers can reverse-engineer the APK and modify it for malicious purposes.
Key Risks
- Lack of obfuscation makes the code easy to analyze
- Reverse engineering exposes API keys and logic
- No protection against debugging or tampering
Mitigation Strategies
- Use code obfuscation to make decompilation harder
- Implement root detection to prevent unauthorized execution
- Detect and block execution in emulated environments
- Use anti-debugging techniques to prevent runtime analysis
8. Security Misconfiguration
Improper configuration of security settings exposes the application to unauthorized access, data leaks, and code execution risks.
Key Risks
- Debugging and logging enabled in production
- Exported activities without proper access controls
- Misconfigured file provider paths allowing access to sensitive files
Mitigation Strategies
- Disable debugging features in the production environment
- Restrict exported activities and enforce proper access controls
- Secure file provider paths and avoid storing sensitive files in shared locations
- Regularly review security configurations in the development lifecycle
9. Insecure Data Storage
Sensitive user data stored insecurely can be extracted by attackers using rooted devices or malware.
Key Risks
- Storing unencrypted sensitive data in local storage
- Insecure session management leading to token theft
- Lack of access control on stored data
Mitigation Strategies
- Use encrypted storage mechanisms (e.g., Keystore, Keychain)
- Avoid storing sensitive data in shared preferences or local databases
- Implement access control and user authentication before accessing stored data
- Regularly clear cached and temporary data
10. Insufficient Cryptography
Weak cryptographic implementations can be exploited to decrypt sensitive data or manipulate app functionality.
Key Risks
- Use of outdated or weak encryption algorithms
- Hardcoded cryptographic keys in the source code
- Lack of data masking and salting techniques
Mitigation Strategies
- Use strong encryption standards (AES-256, RSA-2048, SHA-256)
- Store cryptographic keys securely using hardware-backed keystores
- Implement data masking and salting to enhance security
- Regularly review and update cryptographic implementations
Common Vulnerabilities in Android App
- Insecure Data Storage
- Improper Platform Usage
- Insecure Communication
- Insufficient Authentication / Authorization
- Client-Side Injection
- Security Misconfiguration
- Exposure of Sensitive Information
- Insecure Code Practices
- Improper Session Handling
- 10.Component Vulnerabilities